Business Data Security
Pragmatic, Cost Effective Vulnerability Testing for Business Applications and API's
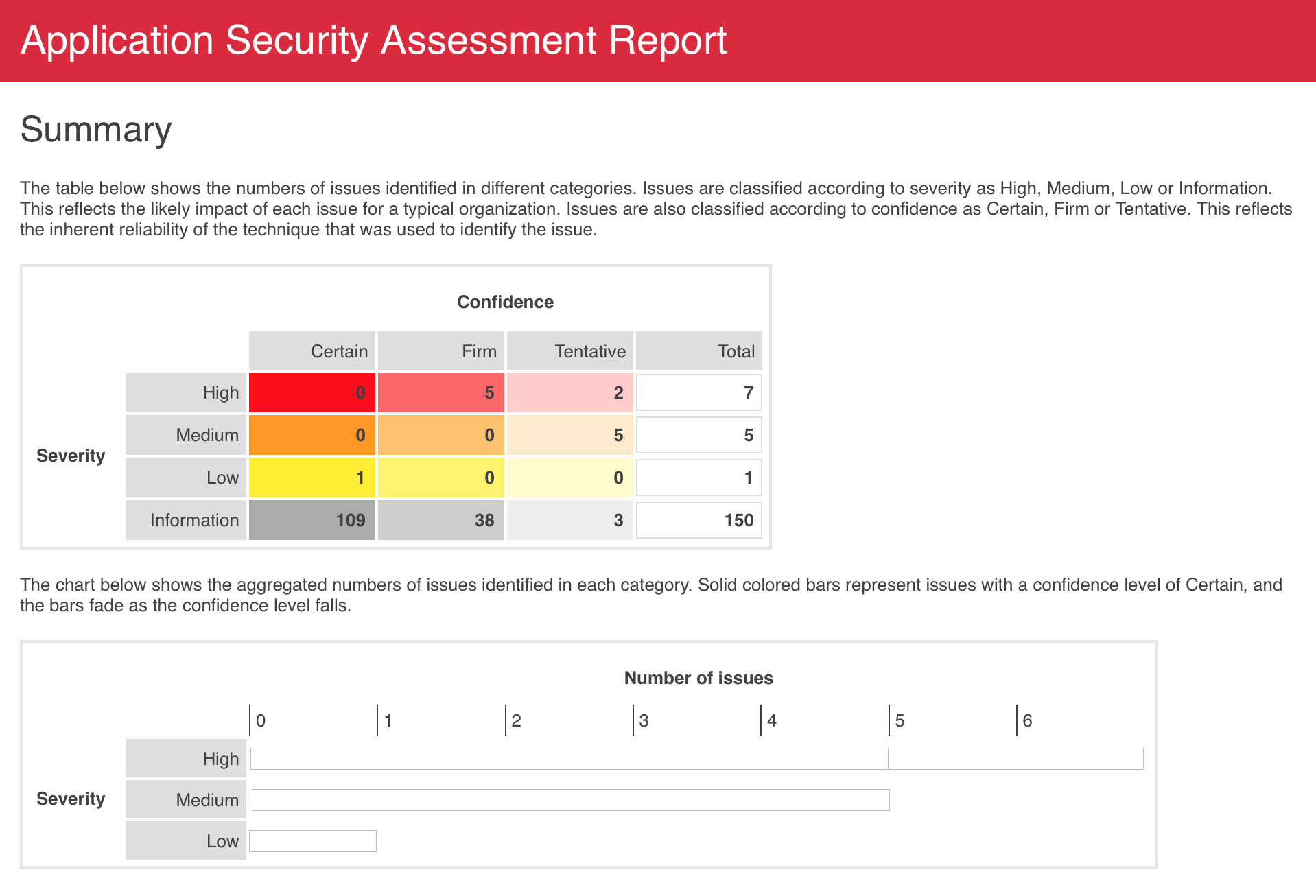
Structured Vulnerability Testing
Main Features
Businesses today are challenged to keep critical information secure within constrained resources and budgets and it is critical to protect assets in most efficient way.
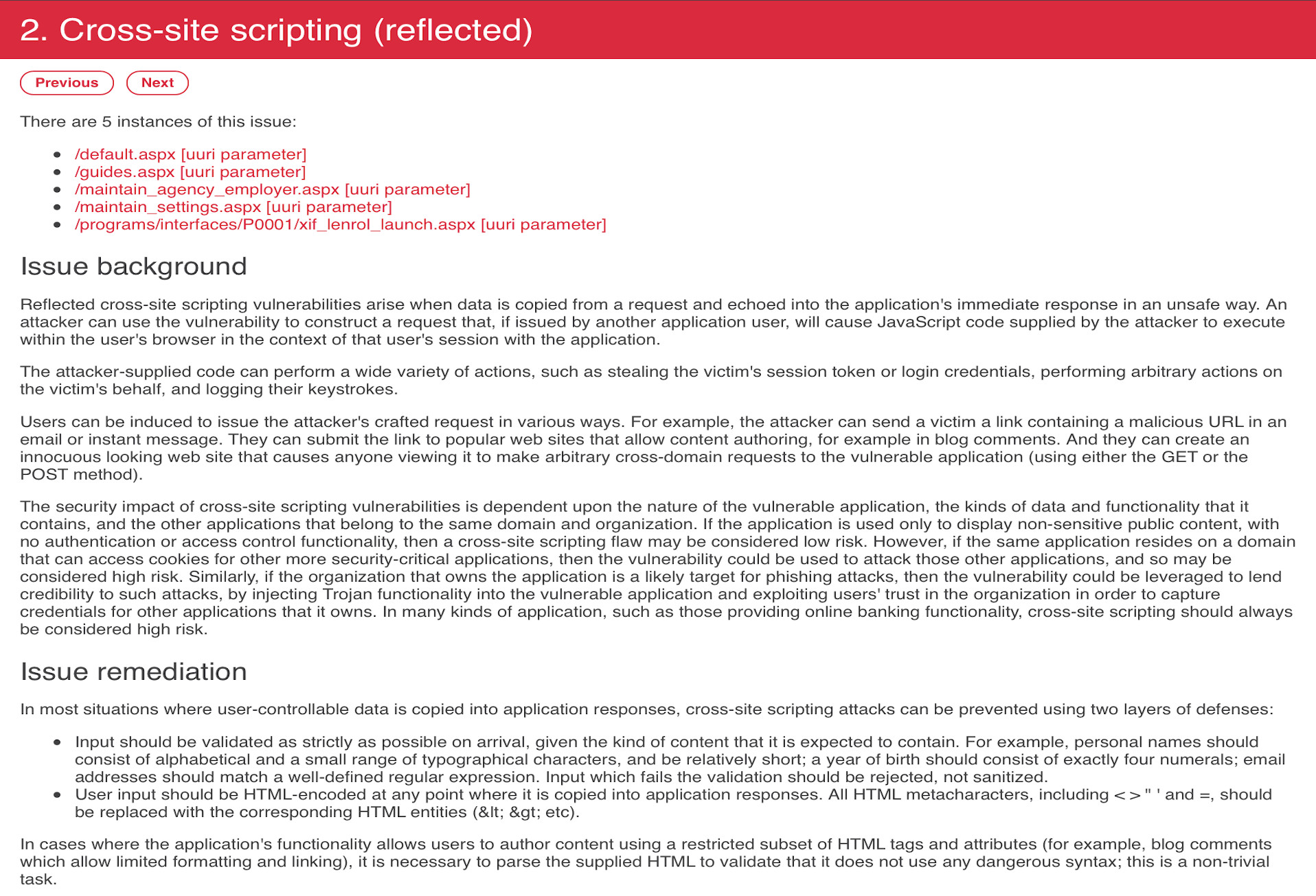
Custom applications are unique to every business and they could be vulnerable to a wide range of malicious attacks which cannot be detected by automatic security scanners.
Our methodology is based on extensive knowledge of common security problems and provides cost effective way to test key components:
Authentication
Session management
Information disclosure
Code injection
Business logic
Infrastructure
API Security
Application and API security assessment
How it works
We use our proven security methodology to concentrate on most critical components responsible for business data security.
All vulnerability assessment activities can typically be accomplished remotely using direct Internet or VPN connectivity.
Steps
- 01Assessment model
- 02Functionality review
- 03Technical review
- 04Initial report
- 05Review findings
- 06Issues mitigation
- 07Final report